[fix] derivative mention and howto
This commit is contained in:
parent
3cd5f05e82
commit
fd909113ed
1 changed files with 21 additions and 6 deletions
27
README.md
27
README.md
|
|
@ -1,6 +1,24 @@
|
|||
# Damn Vulnerable Web Application Docker container
|
||||
[](https://hub.docker.com/r/vulnerables/web-dvwa/)
|
||||

|
||||
|
||||
## Caution
|
||||
|
||||
This is a derivative of the [original project](https://github.com/opsxcq/docker-vulnerable-dvwa/).
|
||||
|
||||
To build your own image :
|
||||
```
|
||||
git clone https://git.interhacker.space/alban/docker-vulnerable-dvwa
|
||||
cd docker-vulnerable-dvwa
|
||||
git submodule init
|
||||
git submodule update
|
||||
docker build . -t dvwa:latest
|
||||
```
|
||||
|
||||
To use the image:
|
||||
```
|
||||
docker run albancrommer/dvwa:latest
|
||||
```
|
||||
|
||||
## About
|
||||
|
||||
Damn Vulnerable Web Application (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goal is to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and to aid both students & teachers to learn about web application security in a controlled class room environment.
|
||||
|
||||
|
|
@ -12,11 +30,10 @@ The aim of DVWA is to practice some of the most common web vulnerability, with v
|
|||
|
||||
To run this image you need [docker](http://docker.com) installed. Just run the command:
|
||||
|
||||
docker run --rm -it -p 80:80 vulnerables/web-dvwa
|
||||
docker run --rm -it -p 80:80 albancrommer/dvwa
|
||||
|
||||
And wait until it download the image and start it, after that you can see the image running in your local machine:
|
||||
|
||||

|
||||
|
||||
Just click on the ```Create / Reset database``` button and it will generate any aditional configuration needed.
|
||||
|
||||
|
|
@ -31,7 +48,6 @@ To login you can use the following credentials:
|
|||
|
||||
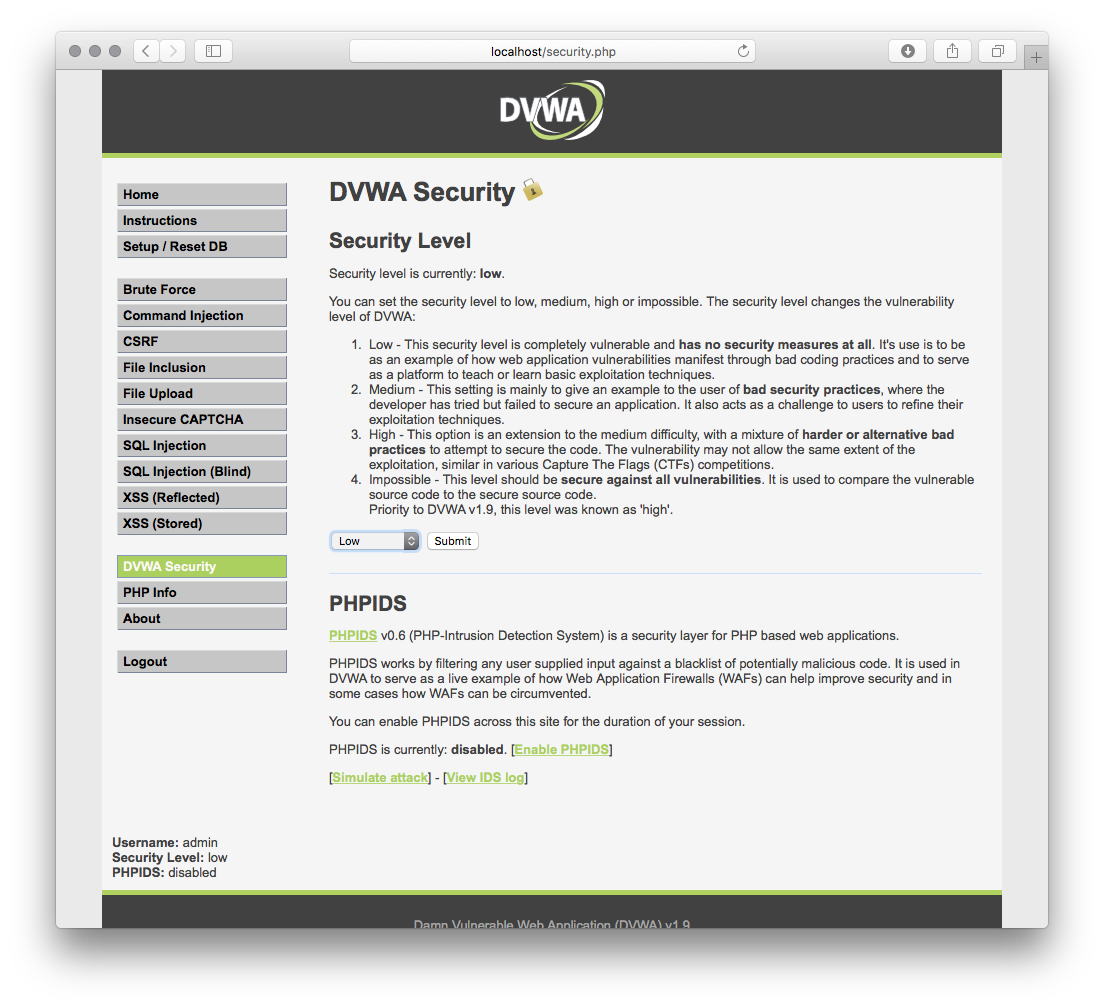
The default dificulty level is the ```impossible``` level, you can change it in ```DVWA Security``` item in the left menu.
|
||||
|
||||
|
||||
|
||||
## Hack and have fun !
|
||||
|
||||
|
|
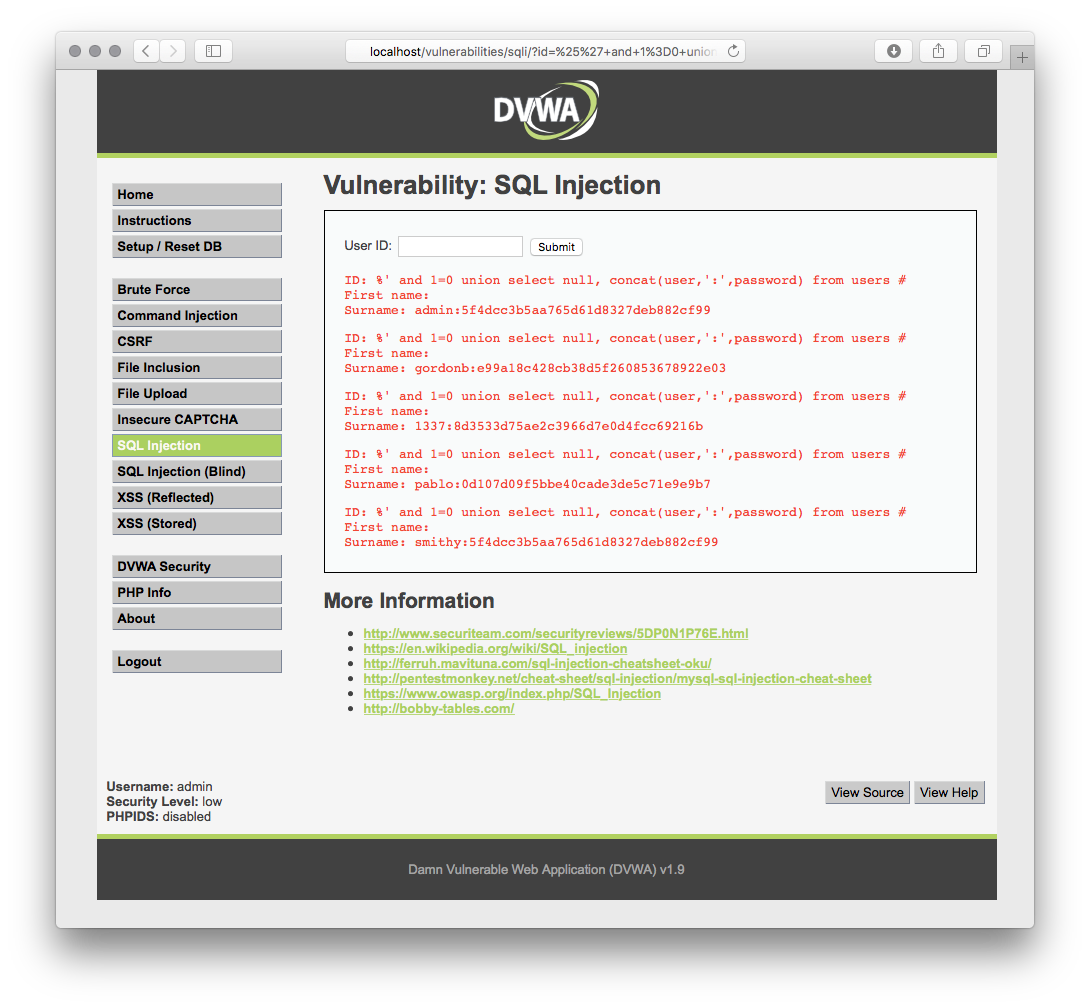
@ -40,7 +56,6 @@ In the id field, add this query:
|
|||
|
||||
%' and 1=0 union select null, concat(user,':',password) from users #
|
||||
|
||||
|
||||
|
||||
There are several other ways and other vulnerabilities do exploit, go ahead, have fun !
|
||||
|
||||
|
|
|
|||
Loading…
Add table
Reference in a new issue